F5 BIG-IP SSL Orchestrator Training Lab > Class 1: SSL Orchestration > Module 2: Inbound SSLO Source | Edit on
Lab 2.1: Inbound Interception Rules¶
Task 1 - Create a new Interception Rule¶
Task 2 - Create Wildcard Listener¶
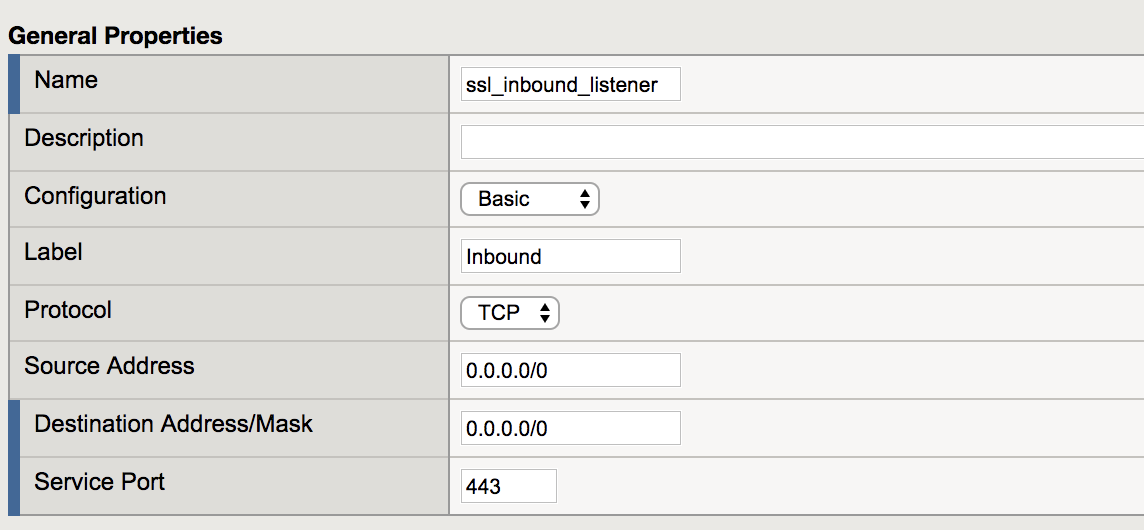
In this step we will create a listener to intercept all inbound HTTPS traffic. After the configuration steps, this will be saved as a wildcard virtual server listening on port 443.
Under the General Properties section, configure the following values:
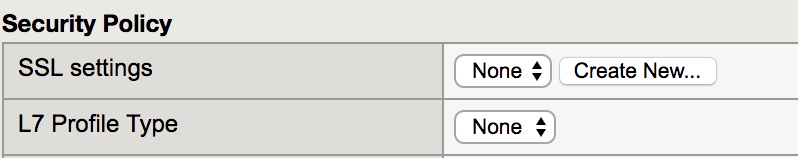
Property Value Name ssl_inbound_listener Destination Address/Mask 0.0.0.0/0 Service Port 443 Under the Security Policy section, select Create New.
The configuration GUI will redirect to the SSL settings configuration page.
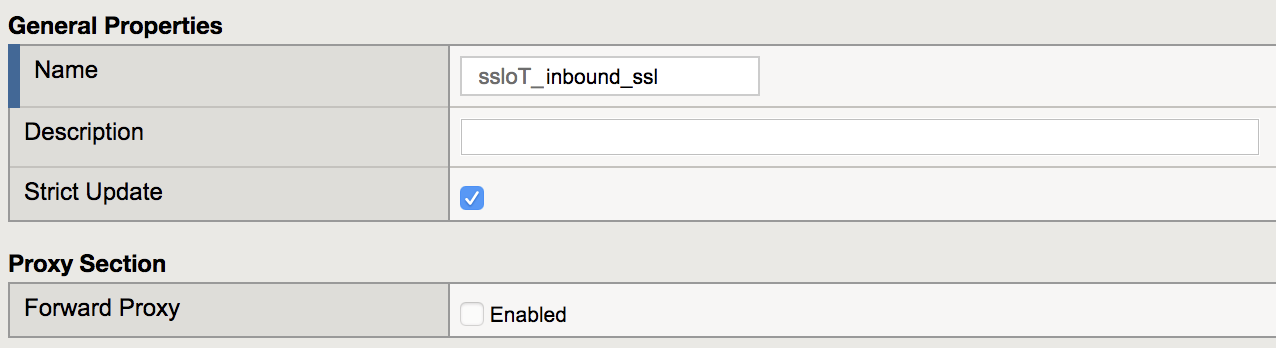
In the General Settings section of the Security Policy, set the name to ssloT_inbound_ssl.
Note
For Inbound configurations the Forward Proxy option should be disabled
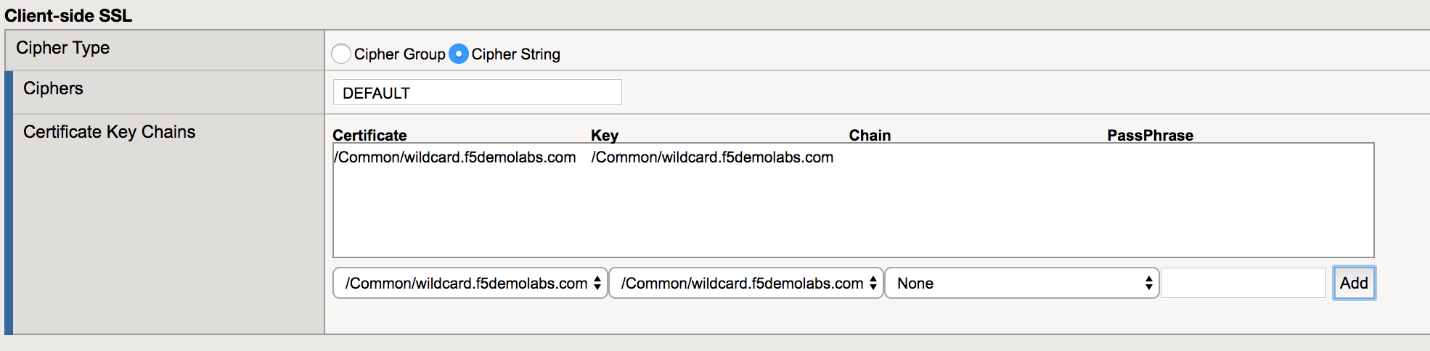
Under the Client-side SSL section, choose wildcard.f5demolabs.com.crt and wildcard.f5demolabs.com.key from the respective drop-down menus and click Add.
Under the section Server-side SSL, configure the following values:
Property Value Expire Certificate Response Control ignore Untrusted Certificate Response Control ignore 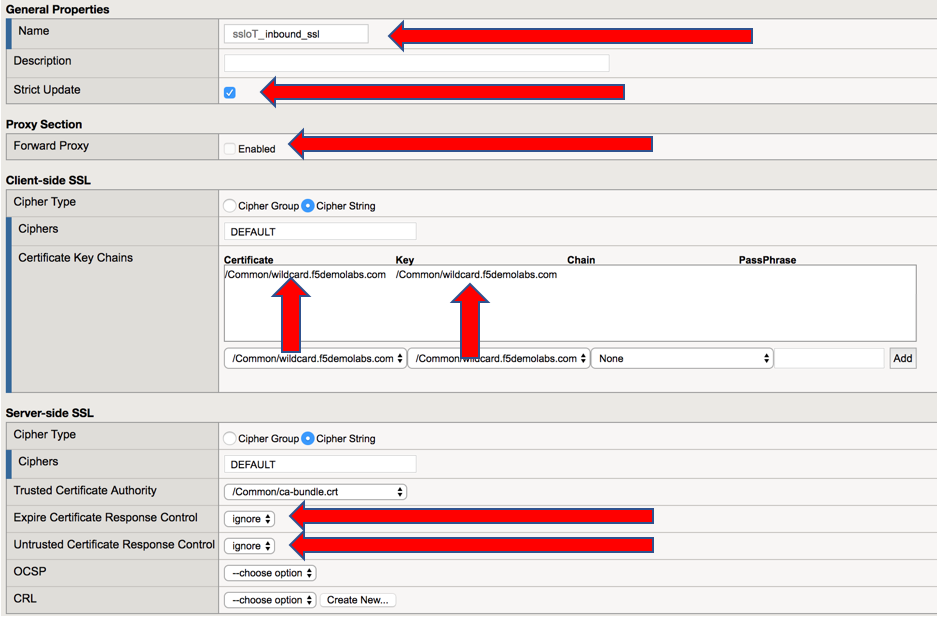
Review the settings and click Finished. This will redirect back to the original Inbound Listener configuration screen.
Task 3 - Configure VLAN Settings¶
In this step, we will define which VLAN interface that our listener will accept connections.
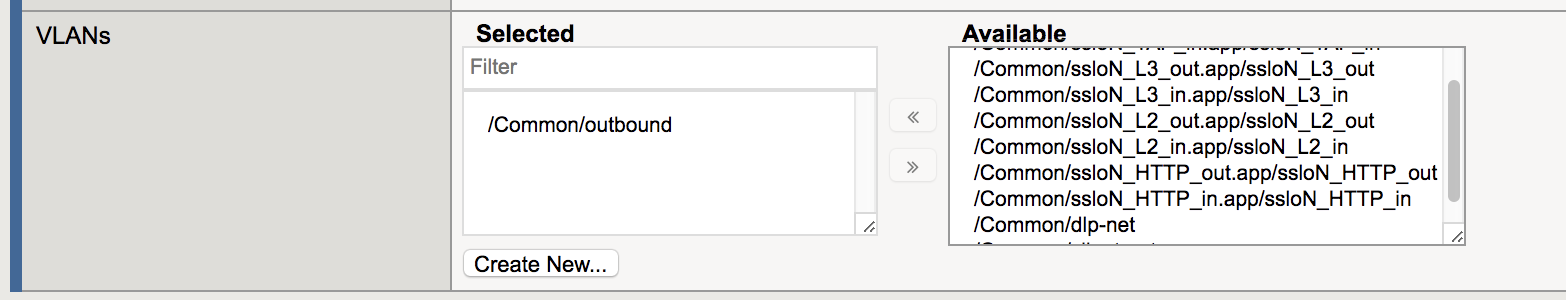
Note
Since we are configuring only for inbound traffic, it is important that the wildcard listener only accept connections on the incoming interface. In this case, the VLAN labeled outbound.
In the VLANs section, choose the /Common/outbound VLAN from the Available List and click the left arrow to move it into Selected.
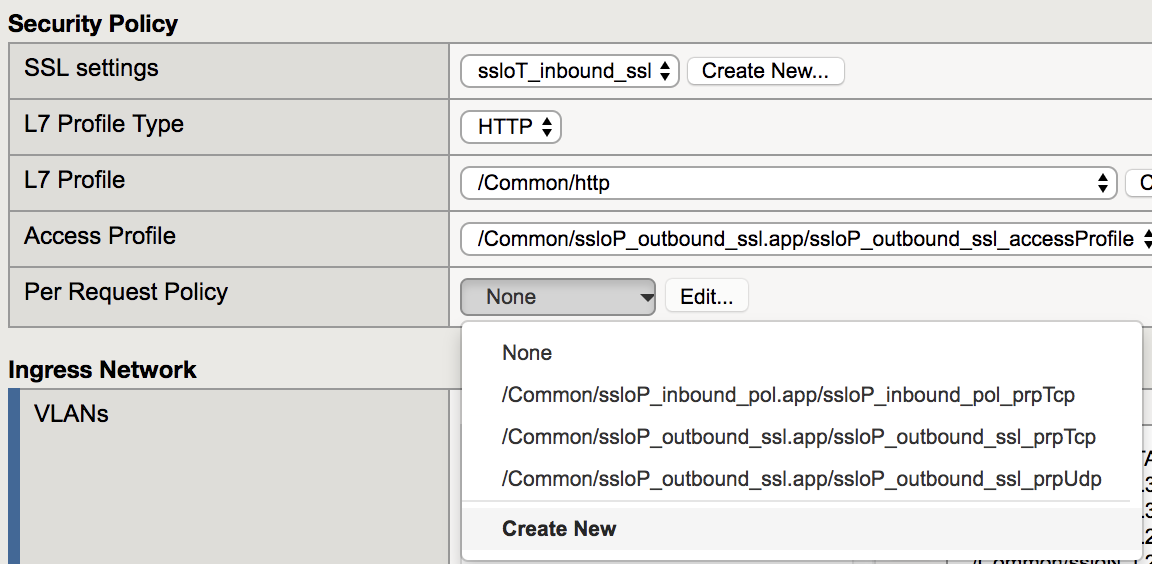
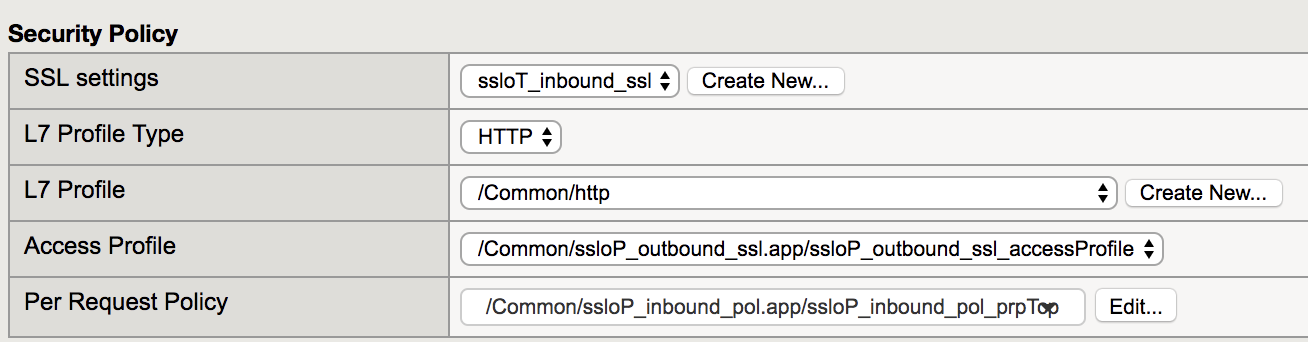
Under the Security Policy section, configure these values:
Property Value L7 Profile Type HTTP L7 Profile /Common/http Access Profile /Common/ssloP_outbound_ssl.app/ssloP_outbound_ssl_accessProfile Per Request Policy Create New Once redirected to the New Inbound Rule configuration:
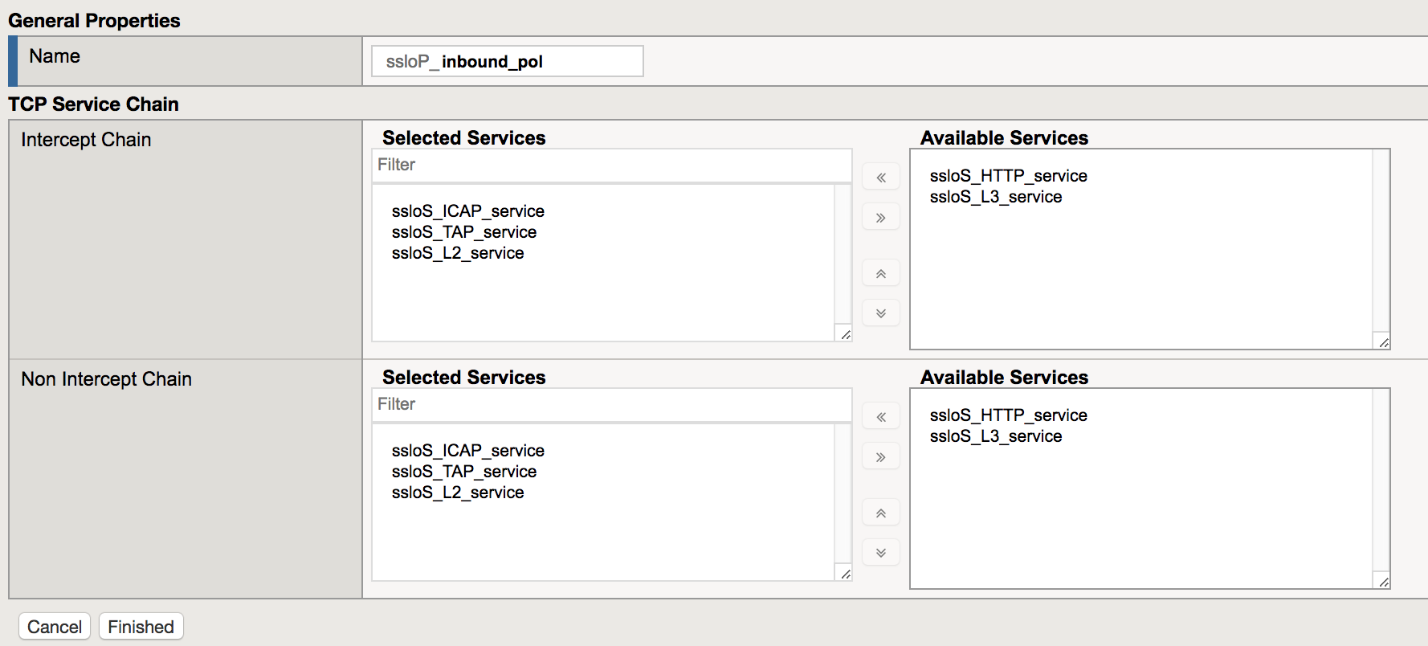
- Create a name for the rule
- Add ICAP, TAP, and L2 services to the Intercept Chain section
- Repeat step (ii) for the Non Intercept Chain
- Click Finished
Verify the settings under Security Policy.
Click Finish